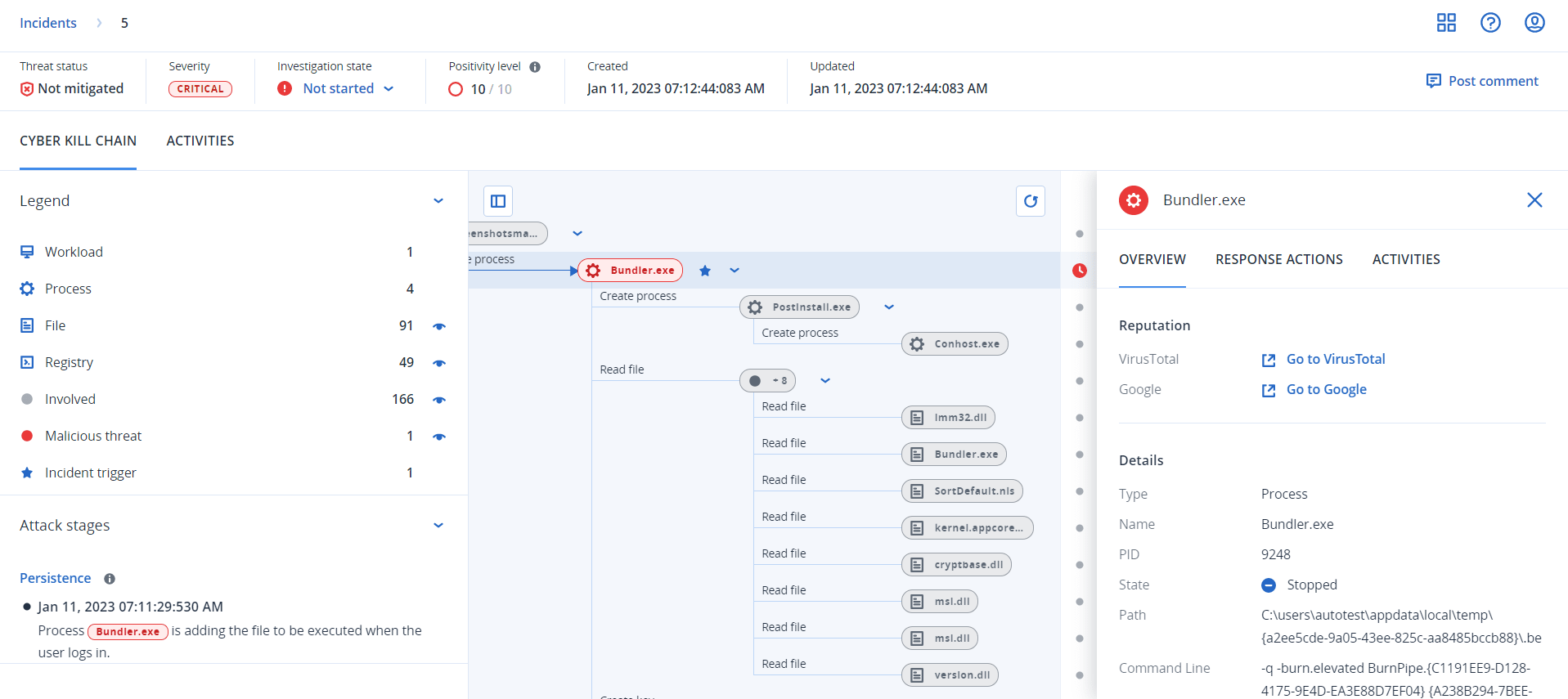
How to investigate incidents in the cyber kill chain
You can investigate each and every step of an attack in the cyber kill chain. Follow the cyber kill chain's easy to comprehend sentences and graphs to understand each step of the attack, which in turn help you to minimize investigation time.
To begin an investigation in the cyber kill chain
- In the Cyber Protect console, go to Protection > Incidents.
-
In the displayed list of incidents, click
 in the far right column of the incident you want to investigate. The cyber kill chain for the selected incident is displayed.
in the far right column of the incident you want to investigate. The cyber kill chain for the selected incident is displayed.
-
View a summary of the incident in the threat status bar at the top of the page. The threat status bar includes the following information:
- Current threat status: The threat status is automatically defined by the system. Any incident that is Not mitigated should be investigated as soon as possible.An incident is set to Mitigated when a restore from backup has been successfully completed or when all detections have been successfully remediated by a stop process, quarantine, or rollback action.
An incident is set to Not mitigated when a restore from backup has not been successfully completed or when at least one detection has not been successfully remediated by a stop process, quarantine, or rollback action. - Incident severity: Critical, High, or Medium. For more information, see Reviewing incidents.
- Current investigation state: One of Investigating, Not started (the default state), False positive, or Closed. You should change the state when you start investigating the incident so that other colleagues are aware of any changes to the incident.
- Positivity level: Indicates how likely an incident is a true malicious attack, between a range of 1-10. For more information, see Reviewing incidents.
- When the incident was created and updated: Date and time the incident was detected, or when the incident was last updated with new detections recorded inside the incident.
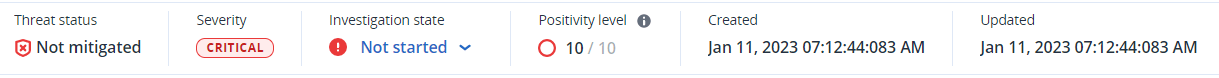
- Current threat status: The threat status is automatically defined by the system. Any incident that is Not mitigated should be investigated as soon as possible.
- Click the Legend tab to view the various nodes that make up the kill chain graph, and define which nodes to view. For further information, see Understanding and customizing the cyber kill chain view.
-
Investigate and remediate the incident by performing the following steps. Note that this is the typical workflow for investigating and remediating an incident, but may vary according to each incident and your own requirements.
- Investigate each stage of the attack in the Attack stages tab. For further information, see Investigate the attack stages of an incident.
Click Remediate entire incident to apply remediation actions. For further information, see Remediate an entire incident.
You can also remediate individual nodes in the cyber kill chain, as described in Response actions for individual cyber kill chain nodes.
- Review actions taken to mitigate the incident in the Activities tab. For further information, see Understand the actions taken to mitigate an incident.
Understanding and customizing the cyber kill chain view
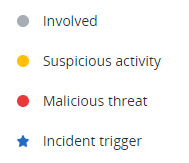
To understand the nodes impacted in the cyber kill chain, access the legend. The legend displays all of the nodes involved in an incident, enabling you to understand how the various nodes have been impacted by the attacker. You can also define the nodes you want to hide or display in the cyber kill chain.
To access the legend
-
Click the arrow icon to the right of the Legend section.
The Legend section expands, as shown below.

-
There are four main colors used in the legend, which enable you to quickly understand what happened to each node in the cyber kill chain, as shown below. These color-coded nodes are also included in the attack stages, as described in Investigate the attack stages of an incident.
To hide or display nodes in the cyber kill chain
- In the expanded Legend section, ensure
 is displayed next to the nodes you want to display in the cyber kill chain. If the displayed icon is
is displayed next to the nodes you want to display in the cyber kill chain. If the displayed icon is  , click the icon to change it to
, click the icon to change it to .
. - To hide a node in the cyber kill chain, click
 . The icon changes to
. The icon changes to  and the node is not displayed in the cyber kill chain.
and the node is not displayed in the cyber kill chain.