Investigate the attack stages of an incident
The attack stages of an incident provide easy to understand interpretations of every incident.
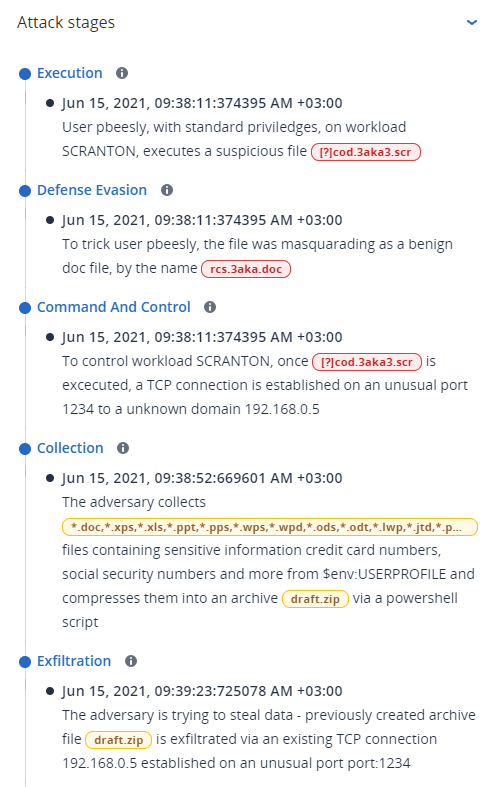
Each attack stage summarizes what exactly happened, and what were the objects (referred to as nodes in the cyber kill chain) targeted. For example, if a downloaded file was masquerading as something else, the attack stage will indicate this, and include links to the relevant node in the cyber kill chain which you can investigate, and to the relevant MITRE ATT&CK technique.
Each stage of the attack provides you with the information you need to resolve three crucial questions:
- What was the attacker's objective?
- How did the attacker achieve this objective?
- Which nodes were targeted?
More importantly, the interpretation provided ensures the time spent on investigating an incident is greatly reduced, as you no longer need to go through each security event from a timeline or graph node and then try to create an interpretation of the attack.
The attack stages also include information about compromised files that contain sensitive information, such as credit card numbers and social security numbers, as shown in the Collection stage in the example below.
For more information, see What information is included in an attack stage?.
How to navigate attack stages
Attack stages are listed in chronological order. Scroll down to see the complete list of attack stages for the incident.
To investigate a specific attack stage further, click anywhere in the attack stage to navigate to the relevant node in the cyber kill chain graph. For more information about navigating the cyber kill chain graph and specific nodes, see Investigate individual nodes in the cyber kill chain.