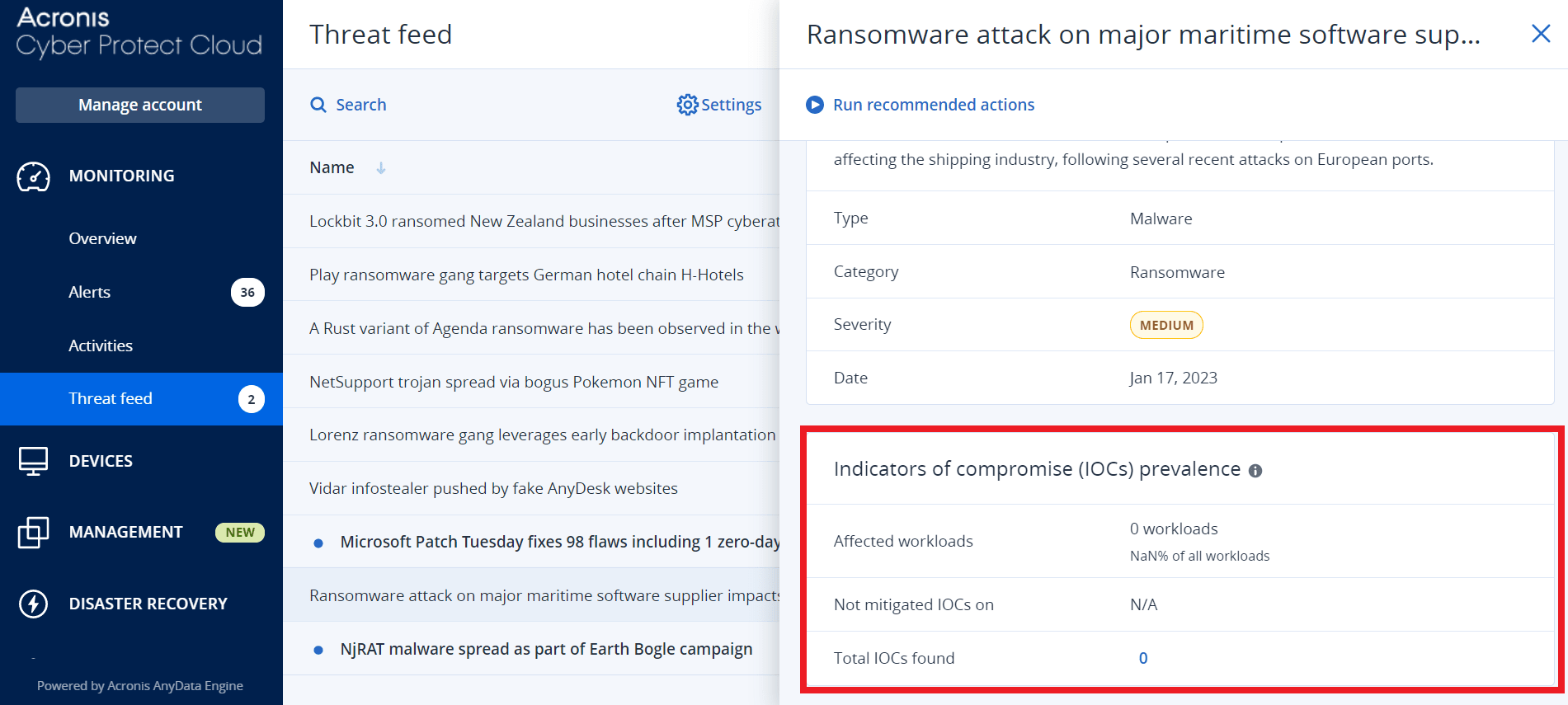
Check for indicators of compromise (IOCs) from publicly known attacks on your workloads
Endpoint Detection and Response (EDR) includes the ability to review existing, known attacks in threat feeds against your workloads. These threat feeds are automatically generated based on threat data received from the Cyber Protection Operations Center (CPOC); EDR enables you to verify whether or not a threat is impacting your workload, and then take the necessary steps to nullify the threat.
You can access threat feeds from the Monitoring menu in the Cyber Protect console. For more information, see Threat feed.
To review specific threat details and confirm if they impact your workloads, click on a threat feed. You can view the number of IOCs detected and workloads affected, and drilldown to workloads that contain unmitigated IOCs.