Site-to-site connection
To understand how networking works in Cyber Disaster Recovery Cloud, we will consider a case when you have three networks with one machine each in the local site. You are going to configure the protection from a disaster for the two networks – Network 10 and Network 20.
On the diagram below, you can see the local site where your machines are hosted and the cloud site where the cloud servers are launched in case of a disaster. The Cyber Disaster Recovery Cloud solution allows you to fail over all the workload from the corrupted machines in the local site to the cloud servers in the cloud. A maximum of five networks can be protected with Cyber Disaster Recovery Cloud.
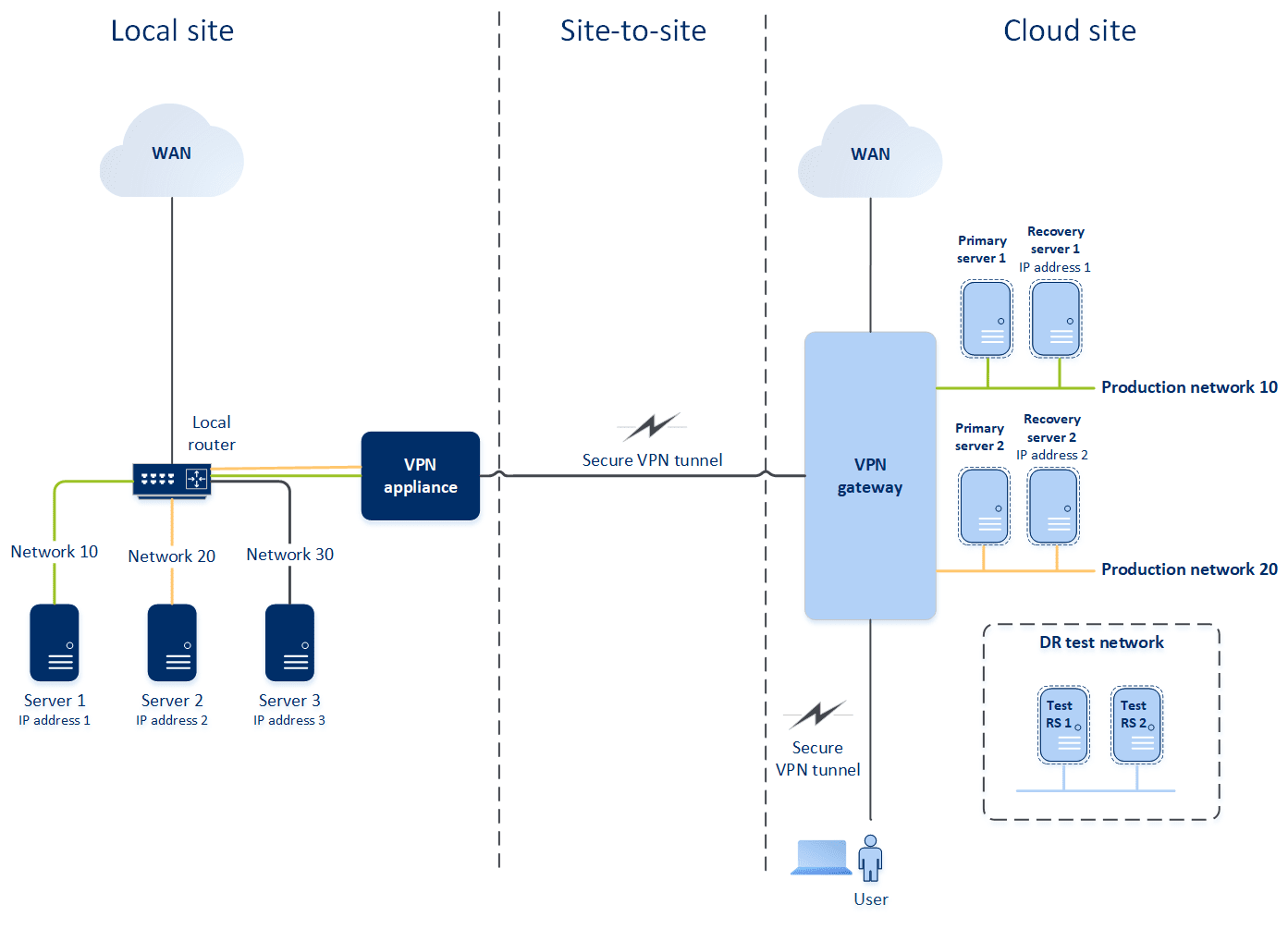
To establish a site-to-site communication between the local and cloud sites, VPN appliance and VPN gateway are used. First, when you start configuring the site-to-site connection in the service console, the VPN gateway is automatically deployed in the cloud site. Then, you must deploy the VPN appliance on your local site, add the networks to be protected, and register the appliance in the cloud. Cyber Disaster Recovery Cloud creates a replica of your local network in the cloud. A secure VPN tunnel is established between the VPN appliance and the VPN gateway. It provides your local network extension to the cloud. The production networks in the cloud are bridged with your local networks. The local and cloud servers can communicate via this VPN tunnel as if they are all in the same Ethernet segment.
For each source machine to be protected, you must create a recovery server on the cloud site. It stays in the Standby state until a failover event happens. If a disaster happens and you start a failover process (in the production mode), the recovery server representing the exact copy of your protected machine is launched in the cloud. It may be assigned the same IP address as the source machine has and launched in the same Ethernet segment. Your clients can continue working with the server, without noticing any background changes.
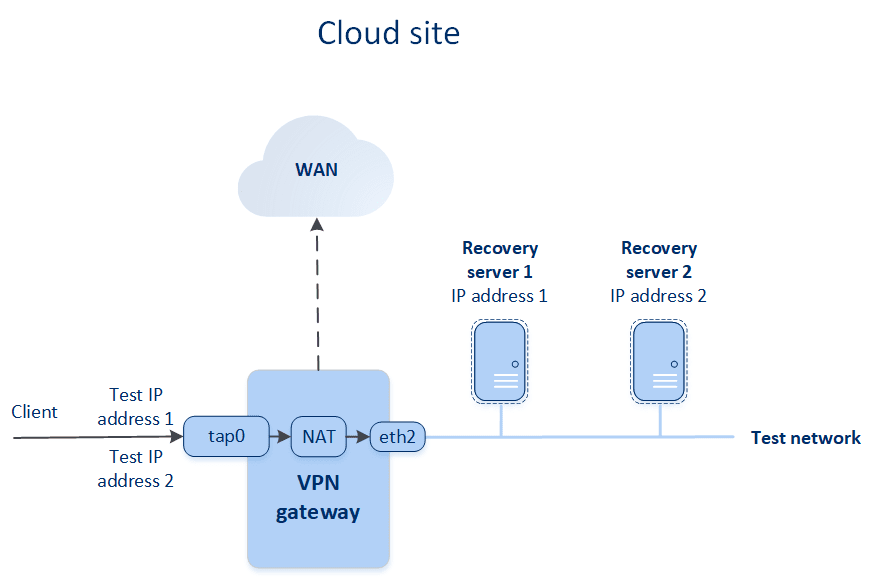
You can also launch a failover process in the test mode. This means that the source machine is still working and at the same time the respective recovery server with the same IP address is launched in the cloud. To prevent IP address conflicts, a special virtual network is created in the cloud – test network. The test network is isolated to prevent duplication of the source machine IP address in one Ethernet segment. To access the recovery server in the test failover mode, you must assign the Test IP address to the recovery server when creating it. There are other parameters for the recovery server that can be specified, they will be considered in the respective sections below.
How routing works
In case of the site-to-site connection established, routing between cloud networks is performed with your local router. The VPN server does not perform routing between the cloud servers located in different cloud networks. If a cloud server from one network wants to communicate to a server from another cloud network, the traffic goes through the VPN tunnel to the local router on the local site, then the local router routes it to another network, and it goes back through the tunnel to the destination server on the cloud site.
VPN gateway
The major component that allows communication between the local and cloud sites is the VPN gateway. It is a virtual machine in the cloud on which the special software is installed, and the network is specifically configured. The VPN gateway provides the following functions:
- Connecting the Ethernet segments of your local network and production network in the cloud in the L2 mode.
- Providing iptables and ebtables rules.
- Working as a default router and NAT for the machines in the test and production networks.
- Working as a DHCP server. All machines in the production and test networks get the network configuration (IP addresses, DNS settings) via DHCP. Every time a cloud server will get the same IP address from the DHCP server. If you need to set up the custom DNS configuration, you should contact the support team.
- Working as a caching DNS.
VPN gateway network configuration
The VPN gateway has several network interfaces:
- External interface, connected to the Internet
- Production interfaces, connected to the production networks
- Test interface, connected to the test network
In addition, two virtual interfaces are added for point-to-site and site-to-site connections.
When the VPN gateway is deployed and initialized, the bridges are created – one for the external interface, and one for the client and production interfaces. Though the client-production bridge and the test interface use the same IP addresses, the VPN gateway can route packages correctly by using a specific technique.
VPN appliance
The VPN appliance is a virtual machine on the local site with Linux and the special software installed, and the special network configuration. It allows communications between the local and cloud sites.
Recovery servers
A recovery server – a replica of the original machine based on the protected server backups stored in the cloud. Recovery servers are used for switching workloads from the original servers in case of a disaster.
When creating a recovery server, you must specify the following network parameters:
- Cloud network (required): a cloud network to which a recovery server will be connected.
- IP address in production network (required): an IP address with which a virtual machine for a recovery server will be launched. This address is used in both the production and test networks. Before launching, the virtual machine is configured for getting the IP address via DHCP.
- Test IP address (optional): this IP address is needed to access a recovery server from the client-production network during the test failover, to prevent the production IP address from being duplicated in the same network. This IP address is different from the IP address in the production network. Servers in the local site can reach the recovery server during the test failover via the test IP address, while access in the reverse direction is not available. Internet access from the recovery server in the test network is available if the Internet access option was selected during the recovery server creation.
- Public IP address (optional): an IP address used to access a recovery server from the Internet. If a server has no public IP address, it can be reached only from the local network.
- Internet access (optional): it allows a recovery server to access the Internet (in both the production and test failover cases).
Public and test IP address
If you assign the public IP address when creating a recovery server, it becomes available from the Internet via this IP address. When a packet comes from the Internet with the destination public IP address, the VPN gateway remaps it to the respective production IP address by using NAT, and then sends it to the corresponding recovery server.
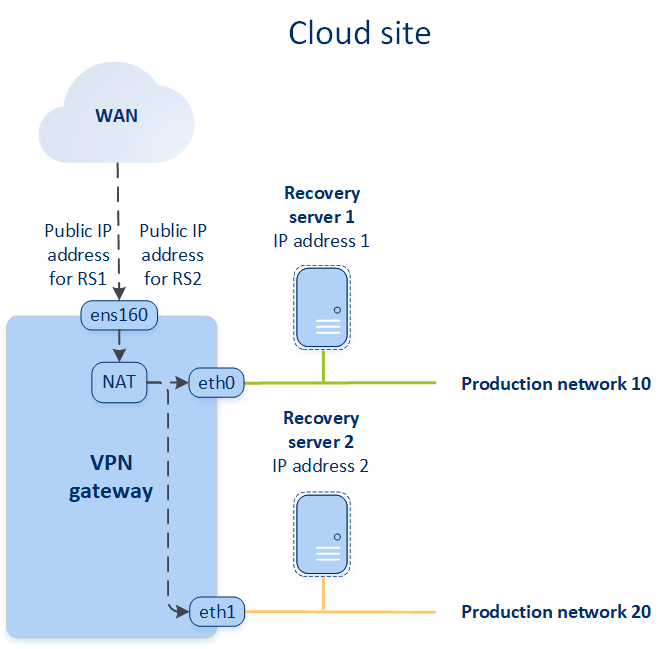
If you assign the test IP address when creating a recovery server, it becomes available in the test network via this IP address. When you perform the test failover, the original machine is still running while the recovery server with the same IP address is launched in the test network in the cloud. There is no IP address conflict as the test network is isolated. The recovery servers in the test network are reachable by their test IP addresses, which are remapped to the production IP addresses via NAT.
Primary servers
A primary server – a virtual machine that does not have a linked machine on the local site if compared with a recovery server. Primary servers are used for protecting an application by means of replication or running various auxiliary services (such as a web server).
Typically, a primary server is used for real-time data replication across servers running crucial applications. You set up the replication by yourself, using the application's native tools. For example, Active Directory replication or SQL replication can be configured among the local servers and the primary server.
Alternatively, a primary server can be included in an AlwaysOn Availability Group (AAG) or Database Availability Group (DAG).
Both methods require a deep knowledge of the application and the administrator rights for it. A primary server constantly consumes computing resources and space on the fast disaster recovery storage. It needs maintenance on your side: monitoring the replication, installing software updates, backing up. The benefits are the minimal RPO and RTO with a minimal load on the production environment (as compared to backing up entire servers to the cloud).
Primary servers are always launched only in the production network and have the following network parameters:
- Cloud network (required): a cloud network to which a primary server will be connected.
- IP address in production network (required): an IP address that the primary server will have in the production network. By default, the first free IP address from your production network is set.
- Public IP address (optional): an IP address used to access a primary server from the Internet. If a server has no public IP address, it can be reached only from the local network, not via the Internet.
- Internet access (optional): allows a primary server to access the Internet.