Forensic data
Malicious activities on a machine can be carried out by viruses, malware, and ransomware. The other case that may require investigations is stealing or changing data on a machine by means of different programs. Such activities may need to be investigated but it is possible only if you keep digital evidence on a machine to investigate. Unfortunately, evidence (files, traces, and so on) may be deleted or a machine may become unavailable.
The backup option called Forensic data allows you to collect digital evidence that can be used in forensic investigations. The following items can be used as digital evidence: a snapshot of the unused disk space, memory dumps, and a snapshot of running processes. The Forensic data functionality is available only for an entire machine backup.
Currently, the Forensic data option is available only for Windows machines with the following OS versions:
- Windows 8.1, Windows 10
- Windows Server 2012 R2 – Windows Server 2019
- After a protection plan with the Backup module is applied to a machine, the forensic data settings cannot be modified. To use different forensic data settings, create a new protection plan.
- Backups with forensic data collection are not supported for machines that are connected to your network through VPN and do not have direct access to the Internet.
The supported locations for backups with forensic data are:
- Cloud storage
-
Local folder
- The local folder is supported only on an external hard disk connected via USB.
- Local dynamic disks are not supported as a location for forensic backups.
- Network folder
Backups with forensic data are automatically notarized. Forensic backups allow investigators to analyze disk areas that are usually not included in a regular disk backup.
Forensic backup process
The system performs the following during a forensic backup process:
- Collects raw memory dump and the list of running processes.
- Automatically reboots a machine into the bootable media.
- Creates the backup that includes both the occupied and unallocated space.
- Notarizes the backed-up disks.
- Reboots into the live operating system and continues plan execution (for example, replication, retention, validation and other).
To configure forensic data collection
- In the service console, go to Devices > All devices. Alternatively, the protection plan can be created from the Plans tab.
- Select the device and click Protect.
- In the protection plan, enable the Backup module.
- In What to back up, select Entire machine.
- In Backup options, click Change.
- Find the Forensic data option.
-
Enable Collect forensic data. The system will automatically collect a memory dump and create a snapshot of running processes.
Full memory dump may contain sensitive data such as passwords.
- Specify the location.
- Click Run Now to perform a backup with forensic data right away or wait until the backup is created according to the schedule.
- Go to Dashboard > Activities, verify that the backup with forensic data was successfully created.
As a result, backups will include forensic data and you will be able to get them and analyze. Backups with forensic data are marked and can be filtered among other backups in Backup storage > Locations by using the Only with forensic data option.
How to get forensic data from a backup?
- In the service console, go to Backup storage, select the location with backups that include forensic data.
- Select the backup with forensic data and click Show backups.
-
Click Recover for the backup with forensic data.
-
To get only the forensic data, click Forensic data.
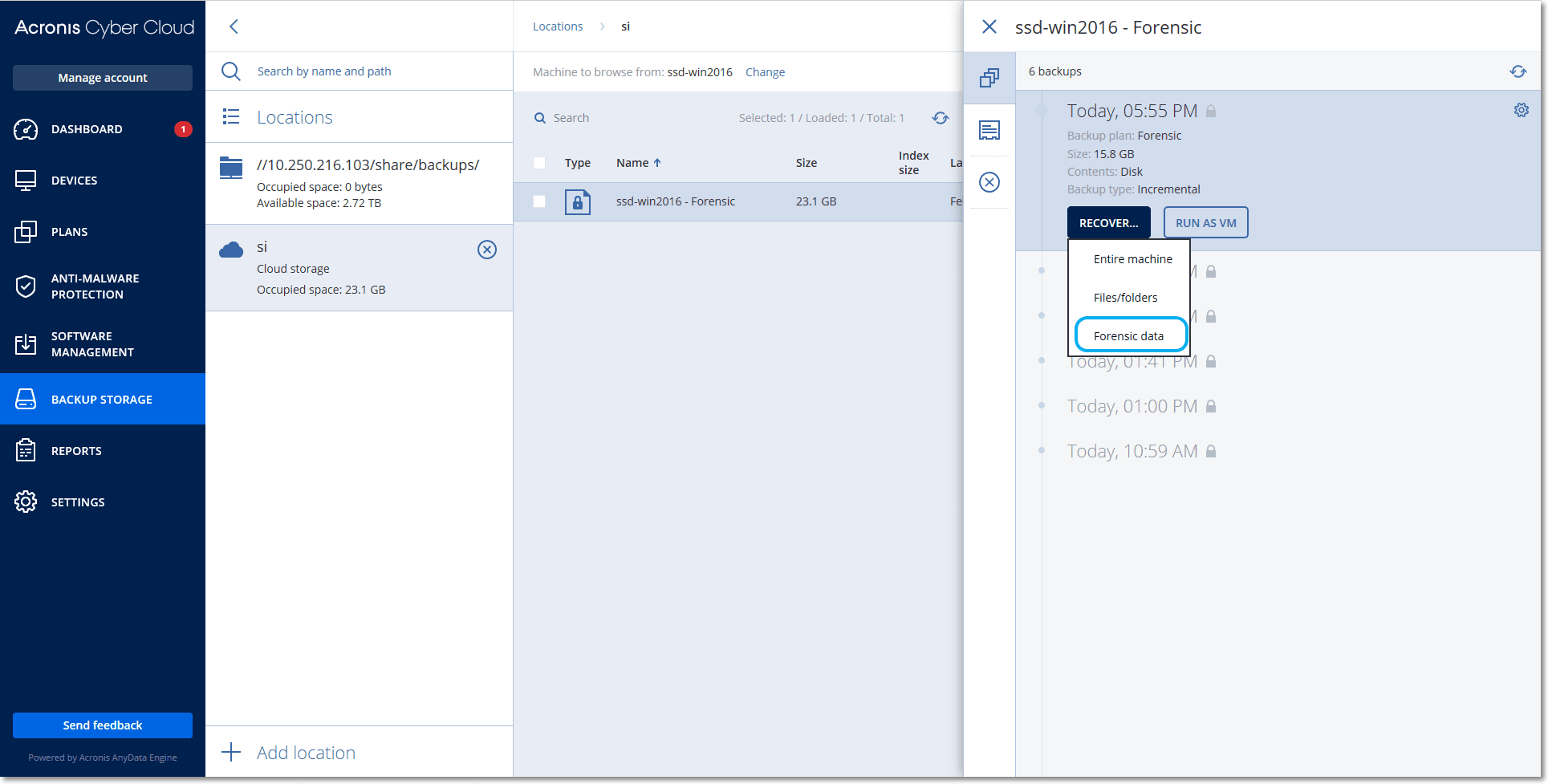
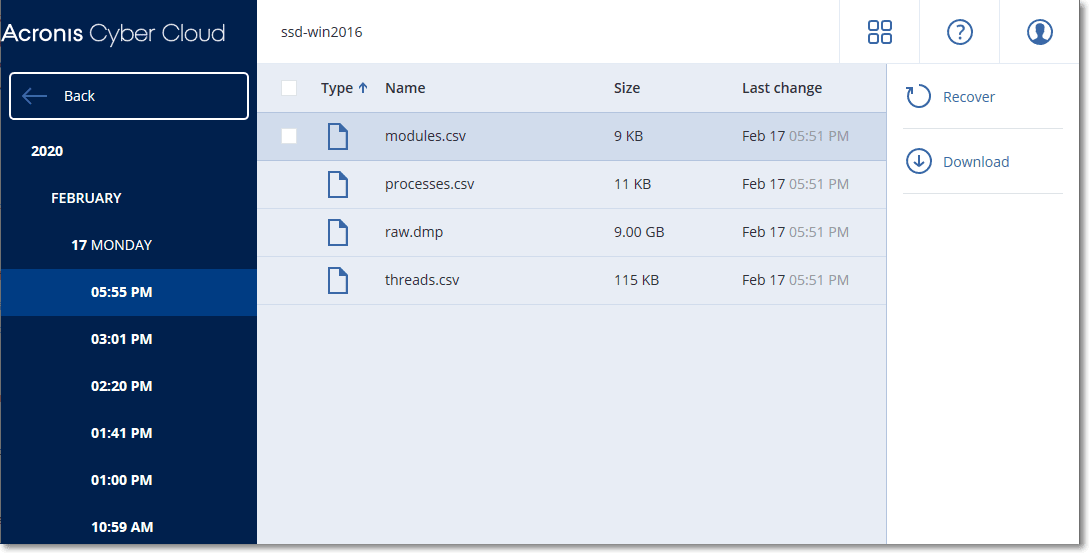
The system will show a folder with forensic data. Select a memory dump file or any other forensic file and click Download.
- To recover a full forensic backup, click Entire machine. The system will recover the backup without the boot mode. Thus, it will be possible to check that the disk was not changed.
-
You can use the provided memory dump with several of third-party forensic software, for example, use Volatility Framework at https://www.volatilityfoundation.org/ for further memory analysis.